
Hello everyone, today I am glad to announce the completion of a patch for the Xbox360-exclusive Arika game Tetris: The Grand Master Ace, as well as an English retranslation of the game’s promotional website ! The patch can be applied to the retail 1.0 release of the game, and translates most if not all the japanese text in the game (I do not have an Xbox Live Gold subscription, or a region-free console, therefore it is impossible for me to verify how well the XBL-exclusive gamemodes work). Here is a short preview of the patch (Xenia’s sound emulation is broken for this game so I turned it off):
And here is one for the flash website:
For the most curious: no, I do not speak Japanese, and I did need to use Google Translate and DeepL a lot in spite of how much I despise MTL translations. Nevertheless, I consider knowing enough about the TGM series to have produced a faithful enough translation. I might get in touch with an actual translator who speaks Japanese once I come up with automated tools that would make it easier to insert text into the game/move it around.
The process mainly involved looking at Japanese/Shift-JIS strings inside of wxMEdit and writing Latin/ASCII text instead. I was pretty lucky that the game allowed to use both text encodings interchangeably, or at the same time if I wanted it to be so. Nowadays, there are a few tools that facilitate the romhacking/modding process of an Xbox360 game.
I – Unencrypting the executable (xextool)
By default, Xbox360 .xex files will most likely be encrypted, as developers would probably wish to protect their retail games.
This is not a problem for us though, as the CLI software xextool can easily decrypt them, and even decompress them in case of compressed games.
xextool -c u default.xex #Uncompresses the file
xextool -c c default.xex #Compress modified file
xextool -e u default.xex #Decrypt the file
xextool -e e default.xex #Ecnrypt modified fileThe resulting decrypted file has text that can be read through. Since the game uses the Shift-JIS encoding, rather than HxD or any other editor that would only have ASCII and a few Latin charsets, we will use wxMEdit. Make sure you go to View > Encoding and select Shift-JIS from there!
II – Analyzing the executable (Ghidra)
Ghidra is an open-source (and free) reverse engineering tool developed by the NSA. This tool allows to “decompile” an executable, and convert its binary data into human-readable pseudocode, as well as many other features. We will use it to locate all of the strings the executable contains, as well as the locations they’re referenced to/used in the program. Due to the astronomical amount of features it presents, as well as the not-so-friendly interface of the program, I would recommend watching/reading a tutorial that explains how it works before getting your hands on the program by yourself. Hilltop’s video is a pretty good start in my opinion. h0x91B is also good, though most of his videos are in Russian and non-subbed.
By default, it couldn’t do much with a .xex file, as it’s mostly used on PC-based executables and architectures in order to help with reversing a virus. Fortunately enough, Ghidra features the ability to create and install custom extensions, making possible the analysis of any architecture, console, or device, that would have such extensions developed.
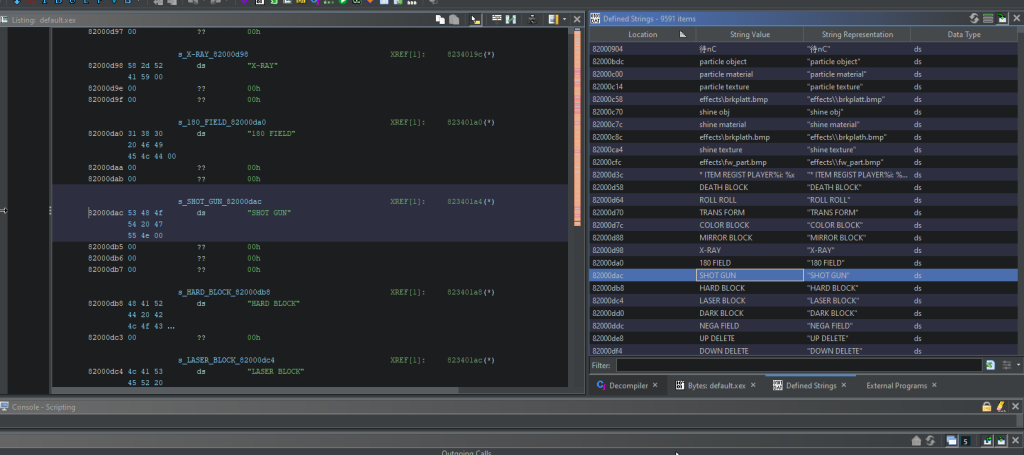
For the Xbox360, XexLoaderWV is the go-to solution. After installing the extension, drag-and-dropping a .xex executable unto Ghidra’s window will allow it to be analyzes. After the analysis is done, Ghidra should point your cursor towards the game’s entry point. We want to go to Search > Encoded Strings… and look for Shift-JIS encoded text. By default it limits the minimal length to 5 characters, I recommend decreasing it all the way down to 3, or even 2 (though that will recognize some data related to code as SJIS strings so beware). Press “Create All” once the strings have been identified. They will now be shown under the section Window > Defined Strings, and clicking any string will show where in the executable it is located.
III – Modifying the executable (wxMEdit)
Ghidra has the ability of analysing the executable, and even “Patching Instructions” in case you want to “modify” the game’s behaviour/data and see how it alters the code’s flow. Nevertheless, it never touches the actual .xex file. To modify it, if you don’t make your own scripts, you will need to use a Hex Editor to meet your ends.
As you might have noticed, something is amiss between what Ghidra tells us, and what we’d see in the actual file. Even though our file is less than 8MB (4MB in TGM Ace’s case), the starting address of every string here is beyond 0x80000000, which makes it harder to see the association between what we see in Ghidra and what we see in a Hex Editor. In order to solve that, take a random string you’ve found before, then locate it in both your executable and ghidra. Substract ghidra’s position from the one you’ve found in the hex editor, and you get the offset you’ll need to apply when carrying over you analysis knowledge to the actual executable.
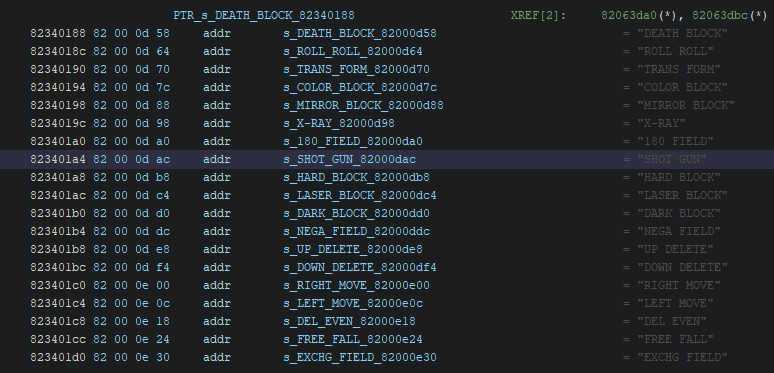
At this point, you will probably ask me why we installed a 500MB tool for cybersec developers when we could just find all of the game’s strings in our hex editor. The first reason, is comfort. With Ghidra, the chance of missing a string is pretty low, all you have to do is scroll through the Defined Strings list and you will be good to go. By using a hex editor alone, you rely on your reading skills to make sure nothing was skipped, which can make you lose plenty of time on the long term.
The second reason, more serious, is that by using Ghidra’s analysis tools, you can detect the pointers (variables that store the address of something) and the chunks of code that refer to a string’s location. In the case of Tetris: The Grand Master Ace this knowledge is pretty important as the pointers related to the strings will decide where our strings begin. What this means, is that if I expect a string at position 0x10 and another at position 0x20, then unless I modify my second string’s pointer afterwards, my first string can never be larger than 15 bytes.
Changing the second string’s pointer so it would expect to find something at position 0x30 instead would allow me to write 16 more bytes into the first one, so it is important to be able to identify, and manipulate those pointers in order to not be limited by the game’s default behaviour.
In my case, there was no need to offset values that much, but from time to time, especially when the initial string was made of no more than three kanji, there was a need to move by 4-5 bytes the addresses of some pointers.
For more advanced romhacks, the game’s assembly can directly be modified if you know what you’re doing, the Xbox360 uses a PowerPC architecture so the instruction set is well-documented, and PowerPC compilers exist in case you want to convert C into X360-compatible assembly rather than writing it by hand. Compiler Explorer gives a good glimpse at how C could be converted to assembly, feel free to play around with the -O compilation options as well.
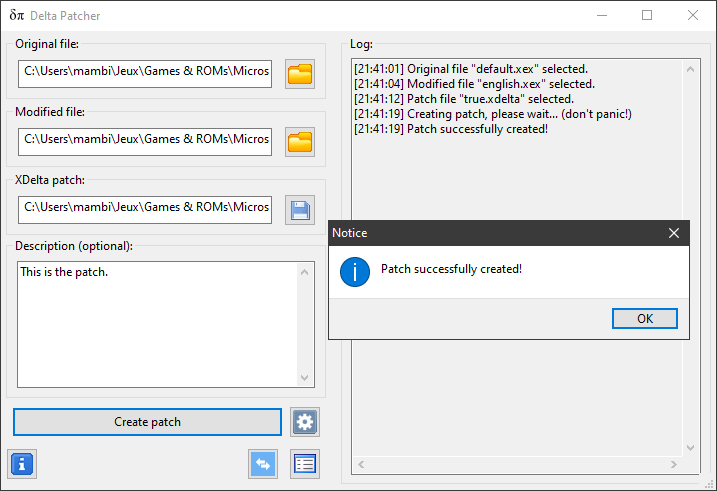
Once you’ve modified all of your strings, saved the custom executable, and tested the game out, it’s time to distribute the executable. The favoured way of doing so is by grabbing your Delta Patcher and creating your own Delta Patch by using the original .xex file as a starting point. Make sure you encrypt/compress your modified file if the original was, and you’re good to go.
Bonus: Translating the original Flash website (JPEXS + Adobe Flash CS6)
If you ever find some cool flash game or animation that’s japanese-only, it’s pretty “easy” to modify it to your liking. The JPEXS Flash Decompiler comes with a tool that allows you to view all the sprites, texts, and scripts of an .swf animation.
It also allows you to use custom fonts, and/or extend the charset the original file supported.

At last, it allows you to modify the game’s texts and behaviour by editing its’ ActionScript logic, and if that is not enough, you can always export the file as an .FLA and edit whatever else you need with Adobe Flash Professionnal CS6. As it is not the main topic of this blogpost, I will not elaborate on it much, but the short tutorials from Serega A. are pretty good, if we omit the disputable game choice that is used as example.
After applying all of his wise teachings, I was able to (almost) fully translate Arika’s flash website from 2005 into English, although I would lie if I said my translation is perfect, be it semantically or even visually.
Conclusion
Thanks to anyone who has read thus far! If you are interested in more writings about romhacking, modding and whatnot, feel free to check the rest of my blog, although my other postings don’t go into much depth about anything related to actual reverse engineering.